 Recently i had my smaller blogs on a shared server hacked and injected with mailicious code. I hadn’t updated any scripts on any of these sites as i wasn’t posting much content on them.
Recently i had my smaller blogs on a shared server hacked and injected with mailicious code. I hadn’t updated any scripts on any of these sites as i wasn’t posting much content on them.
Tim Thumb Files Exploited
Below is a copy of an email i received from Bluehost who have taken the liberty of fixing the problem and advise me to update all scripts now.
Dear customer,
This is a courtesy notice that we have found and corrected exploitable timthumb.php file(s) on your australia-wine.com account, which are listed below.
While we have corrected these files, we do recommend you ensure all potential exploits are corrected on your account. This is best done by updating all scripts, plugins, modules and themes on your account to the latest version.
As the owner of the account, you are responsible for keeping your hosted content free of malicious software. For technical assistance, you can also reach our chat team from Bluehost.com or by going directly to:
The timthumb.php file is a script commonly used in WordPress’s (and other software’s) themes and plugins to resize images.
The exploit allows an attacker to arbitrarily upload and create files and/or folders on your account, which can then be used for a number of malicious tasks, including but not limited to defacement, browser high-jacking and infection, data harvesting and more.
After a site has been exploited, it may lead to becoming labeled a “Malicious Website” by Google or other security authorities.
Any timthumb.php file below version 1.35, but above version 1.09 is considered vulnerable, unless patched. To prevent being compromised, we advise you update all instances of timthumb.php to version 2.0, or patch the existing vulnerable files.
Note that patching the files requires more in-depth knowledge of the PHP scripting language.
The updated version of timthumb.php can be found here:
http://timthumb.googlecode.com/svn/trunk/timthumb.php
We have automatically patched the following files for you:
Additional information regarding the compromise can be found at the following two websites, as well as others; note that all external websites in this email are not affiliated with Bluehost.com in any capacity, and are for your reference only.
http://markmaunder.com/2011/08/01/zero-day-vulnerability-in-many-wordpress-themes/
http://redleg-redleg.blogspot.com/2011/08/malware-hosted-newportalsecom.html
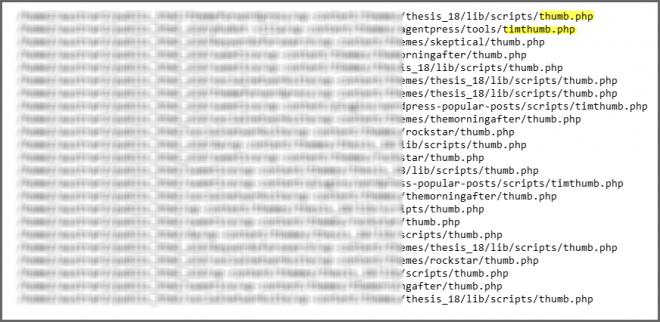
You can clearly see from the screenshot above that there are multiple files effected including inactive themes and plugins.
WordPress .htaccess File Security
This hacking includes infected .htacces files which where injected with malicious redirects to a site distributing malware. Google then blacklisted these blogs which resulted in a warning being displayed in the Google SERPS as well as on each site itself.
I’ve already written about one solution to secure and backup your .htaccess files however there are other solutions available via security plugins and manual solutions.
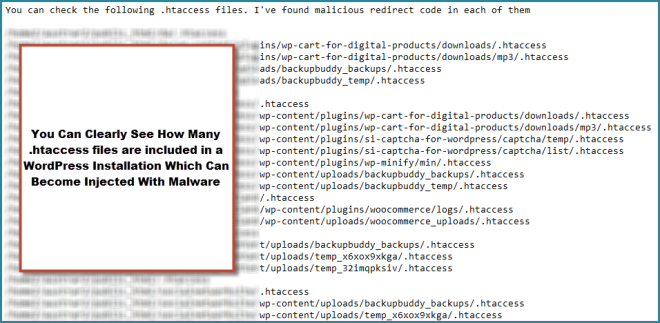
Here’s a screenshot of the infected .htaccess files
I was lucky i took full backup of all these sites and stored them away from the server or the backups could have been injected as well. The Bluehost account i use to host these sites is also a Pro account meaning i had access to daily, weekly and monthly backups.
The monthly backups where Not infected which mean’t i could easily restore these after deleting the infected files and then update all scripts immediately afterwards to avoid another injection.
If i had only been using a standard shared hosting account and not kept full backups offsite, the solution could have been very costly.
I’ve already written about why its crucial to update WordPress scripts and secure your WordPress site previously and this latest injection of malware only reinforces these security issues further.
There are several ways to scan your WordPress installations to secure your WordPress sites, one of which can be completed using a plugin named website defender.
I was abit surprised Bluehost helped me fix these problems after receiving this email previously.
Although we host your website, we are unable to manage security of your content. We have multiple safeguards in place to prevent our servers from being hacked, including prevention against brute force attacks and tight security on user accounts.
The actual vulnerabilities a hacker uses to gain access to your home directory or public_html folder are often located in the scripts themselves.
For this reason, we provide updates through SimpleScripts as they are made available, and also offer courtesy server backups and a backup utility in cPanel, which you can use to take partial or full snapshots of your account whenever you feel a need.
As to which script was exploited to allow access to your account, we would be uncertain what was used, as most exploits use standard pages in your account with unusually formed requests to inject their own content to your site.
There are multiple resources online to help you identify the cause, and we would suggest starting with the authors of the software you are running, to see if there are known exploits or updates that the vendor is aware of.
Here is a security checklist that you can review which can greatly help secure your account sites:
- Change the Admin Email on your account.
- Change the Password on your account.
- Change the Credit Card on file on your account.
- Update and apply any patches, upgrades, or updates that the 3rd party vendor or web developer of your scripts may have available.
- Fix any loose file permissions (this may be the most common exploit vulnerability) 6. Delete all non-system Ftp Accounts that were created, or at the very least, change the passwords to the FTP Accounts.
- Remove any Access Hosts by clicking the “Remote Mysql” icon and clicking the Remove Red X by each entry if there are any entries.
- Check your scripts for any Header Injection attacks, Sql Injection attacks, Cross-Site Scripting attacks, etc., as well as your php.ini file settings.
- Check your home/work computers for any viruses, trojans, or keyloggers.
If your scripts are infected, you may want to rollback to the last good snapshot backup of your account. If your backups are also infected, then you may want to consider having us reset your account to start afresh.
Securing your scripts and securing your PC are both your responsibility.
The programs that operate database-driven sites are vulnerable to hackers, who can (and do) exploit bugs in those programs to gain unauthorized access to your site. While our servers are exceptionally secure, your scripts may not be.
The best course of action is to always keep your scripts updated, your code clean, and your passwords secure. Here are some steps that can help you secure your site.
There are only two ways that an account can get infected:
- You are running an insecure script on your account that is used to break in.
- Your computer is infected and they have hacked into your account through your own computer, or by grabbing your password.
Securing your scripts and securing your PC are both your responsibility.
We do offer updates via our Simple Script tool in cpanel if this is what you used to install your scripts to help keep them secure. Here are some steps that can help you secure your site.
Here is our site security checklist to help in securing the account :
- https://my.bluehost.com/cgi/help/511
- Tips for Cleaning & Securing your Website – StopBadware.org http://www.stopbadware.org/home/security
How to remove the “This site may harm your computer”
How to prevent your site from getting hacked. How to repair a damaged site.
Website security precautions
Prevention
- These malicious hacking and malware injections could have been avoided by updating all plugins, themes and scripts.
- Always create and store regular full backup of all your WordPress installations offsite in a secure location.
- Install and run an anti virus software on your local computer
- Personally i’ve found Google Chrome more insecure than I.E or Firefox

You must be logged in to post a comment.